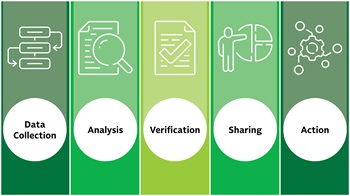
<p>By: Doug Baker, Vice President, Industry Relations, FMI</p><p><img src="https://www.fmi.org/images/default-source/blog-images/key-stages-of-threat-assessment.tmb-large-350-.jpg?Culture=en&sfvrsn=98dba2d7_1" style="float:right;margin:10px;" class="-align-right" alt="Key Stages of Threat Assessment graphic" sf-size="438227" /></p><p>The food industry faces a range of security threats, from cyberattacks and supply chain disruptions to organized retail crime and fraud. A robust threat intelligence program is critical for safeguarding operations, protecting assets and ensuring business continuity. But what does effective threat intelligence look like? Here are the five key stages of threat intelligence: </p><h5>1. Data Collection: Building the Foundation</h5><p>Effective threat intelligence begins with gathering relevant data from a variety of sources, including internal security systems, industry reports, law enforcement bulletins and open-source intelligence. For food retailers and suppliers, this may include monitoring dark web activity for signs of fraud, tracking patterns in theft and organized crime, and keeping tabs on regulatory updates that could impact operations.</p><h5>2. Analysis: Turning Data into Intelligence</h5><p>Raw data alone is not helpful without proper analysis. Security professionals must assess and contextualize the information to understand potential risks. For example, if a particular geographic region is experiencing a surge in organized retail crime, analyzing trends can help predict where the next incidents may occur. This step requires leveraging technology, such as artificial intelligence and data analytics tools, to identify patterns and anomalies.</p><h5>3. Verification: Ensuring Accuracy and Relevance</h5><p>Not all intelligence is actionable. Verification is a crucial step to weed out misinformation and ensure that only credible, high-priority threats are escalated. Cross-referencing intelligence with trusted industry sources, law enforcement and third-party security providers helps confirm the legitimacy of threats and prevents organizations from acting on false alarms.</p><h5>4. Sharing: Strengthening Industry Collaboration</h5><p>Threat intelligence is most effective when shared. The food industry thrives on collaboration, and the same principle applies to security. Organizations should participate in industry networks, such as FMI’s asset protection initiatives, to exchange intelligence on emerging threats. Establishing relationships with law enforcement, regulatory bodies and industry peers enhances situational awareness and strengthens collective resilience.</p><h5>5. Action: Mitigating Risks Proactively</h5><p>The final and most critical stage is turning intelligence into action. This could mean adjusting security protocols, investing in technology solutions, conducting employee training, and/or implementing supply chain safeguards. A proactive approach ensures that organizations stay ahead of threats rather than reacting after incidents occur.</p><p>At the <a href="https://www.fmi.org/asset-protection-and-grocery-resilience-conference">2025 Asset Protection & Grocery Resilience Conference</a>, March 21 – April 3, industry experts will dive deeper into best practices for threat intelligence, loss prevention, and risk mitigation strategies tailored for the food industry. Register today to ensure your organization is prepared for the evolving security landscape.</p><p><a href="https://www.fmi.org/asset-protection-and-grocery-resilience-conference" class="button">Register Now</a></p>
[#item_full_content]